There are various ways to make unauthorized modifications to any mobile device to overcome limitations imposed by mobile service providers. This process is called ____.
A. extraction
B. rooting
C. jailbreak
D. hacks
Answer: B
You might also like to view...
(Order of Exception Handlers) Write a program illustrating that the order of exception han- dlers is important. The first matching handler is the one that executes. Attempt to compile and run your program two different ways to show that two different handlers execute with two different ef- fects.
What will be an ideal response?
A function such as NOW that is updated each time a workbook is opened is said to be:
A) conditional. B) filtered. C) frozen. D) volatile.
As long as you pick the correct chart you can mix numeric value systems, such as dollars and number of units sold
Indicate whether the statement is true or false
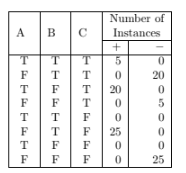
According to the classification error rate, which attribute would be chosen as the first splitting attribute? For each attribute, show the contingency table and the gains in classification error rate.
The following table summarizes a data set with three attributes A, B, C and
two class labels +, ?. Build a two-level decision tree.