The __________ vulnerability assessment is designed to find and document vulnerabilities that may be present in the organization's wireless local area networks.
Fill in the blank(s) with the appropriate word(s).
wireless
Computer Science & Information Technology
You might also like to view...
The biggest advantage of Voice over Internet Protocol (VoIP) is _____.
A. ?cost savings B. ?voice clarity C. ?high-quality streaming of movies and television shows D. ?0% downtime
Computer Science & Information Technology
?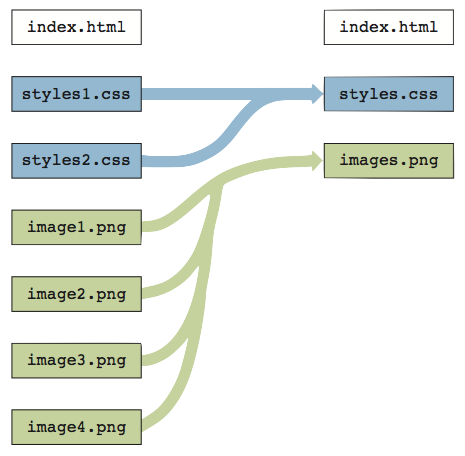
A. removing orphaned styles. B. reducing the number of HTTP requests. C. minifying CSS files. D. implementing spritesheets.
Computer Science & Information Technology
Which of the following comes with a built in local firewall?
A. Windows 7 B. Windows 6 C. Windows XP D. Windows Vista
Computer Science & Information Technology
What are the actions an antivirus software package might take when it discovers an infected file?
What will be an ideal response?
Computer Science & Information Technology