In the __________ attack, an attacker monitors (or sniffs) packets from the network, modifies them, and inserts them back into the network.
A. zombie-in-the-middle
B. sniff-in-the-middle
C. server-in-the-middle
D. man-in-the-middle
Answer: D
You might also like to view...
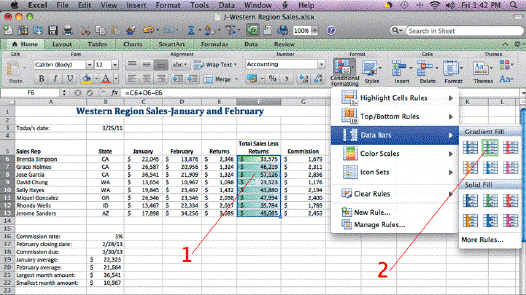 Applying data bars to selected cells, as shown in the accompanying figure, is an example of ____.
Applying data bars to selected cells, as shown in the accompanying figure, is an example of ____.
A. conditional formatting B. statistical formatting C. formula formatting D. numeric formatting
________ is the search engine that is included with Windows 10
A) Yahoo B) Google C) DuckDuckGo D) Bing
You can print a filtered table.
Answer the following statement true (T) or false (F)
Answer the following statement(s) true (T) or false (F)
1. Spikes at the left in a histogram indicate potential highlight clipping. _________________________ 2. In a histogram, the Highlight clipping warning icon is displayed at the left of the histogram. _________________________ 3. In a histogram, the Shadow clipping warning icon is displayed at the right. _________________________ 4. Toggling a clipping warning icon off and on can help you identify the pixels that may be affected by clicking. _________________________