The ____ approach for detecting intrusions is based on the frequency with which certain network activities take place.
A. signature-based IDPS
B. knowledge-based IDPS
C. anomaly-based IDPS
D. host-based IDPS
Answer: C
You might also like to view...
The ____ controls the output voltage of the AC generator, based on charging system demands, by controlling field current.
A. starter relay B. ignition switch C. current generator D. voltage regulator
Technician A says that work is defined as actually accomplishing movement when force is applied to an object. Technician B says that torque is not a form of work. Which technician is correct?
A) Technician A only B) Technician B only C) Both technicians D) Neither technician
Refrigerant that has been reprocessed to at least the purity specified in ARI Standard 700 is considered:
A) Recovered refrigerant. B) Recycled refrigerant. C) Reclaimed refrigerant. D) Virgin refrigerant.
Carry the answer to four decimal places. The lighting set shown has the same number of volts across each lamp. The sum of all lamp voltages is equal to the total number of volts. Find the number of volts across each lamp.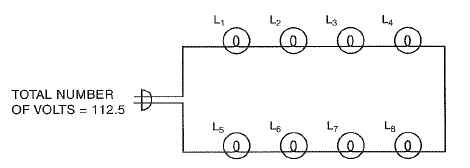
Fill in the blank(s) with the appropriate word(s).