Which of the following is a type of third-party network troubleshooting tool? (Select all that apply.)
A. port scanner
B. ipconfig
C. packet sniffer
D. traceroute
E. both A and C
Answer: E
You might also like to view...
When the number of instructions of an algorithm is bounded by a constant, it means that:
A. the execution time of the algorithm would be very high B. the number of instructions are bound to be constant C. every time the algorithm runs, the same number of instructions are executed D. there is an upper limit to the number of instructions executed
A counter is a(n) ____________ that can be incremented or decremented each time a loop runs.
a. string variable b. condition c. integer variable d. property
A company that transmits data over the telephone is con- cerned that its phones could be tapped. All its data is transmitted as four-digit int values. The company has asked you to write an application that encrypts its data so that the data may be transmitted more securely. Encryption is the process of transforming data for security reasons. Your application should read a four-digit integer input by the user in a JTextField and encrypt the information as described in the steps of this exercise when the user clicks the Encrypt JButton (Fig. 6.35).
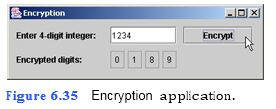
```
a) Copying the template to your working directory. Copy the C:Examples Tutorial06ExercisesEncryption directory to your C:SimplyJava directory.
b) Opening the template file. Open the Encryption.java file in your text editor.
c) Coding the Encrypt JButton’s ActionPerformed event handler. Add the code for Steps d through f to event handler encryptJButtonActionPerformed (lines 138–141).
d) Obtaining the user input. In line 140, insert a statement that obtains the user input from numberJTextField, converts it to an int and assigns the value to int variable number.
e) Extracting the digits from the user input. Use the programming techniques you used to solve Exercise 5.17 to insert statements that extract the digits from int variable number. Store the digits of number in the int variables digit1, digit2, digit3 and digit4, respectively.
f) Encrypt each digit and display the encrypted results. Replace each digit by perform- ing the calculation (the sum of that dig
An advantage to making a method ____ is that the compiler knows there will be only one version of the method.
A. inheritable B. private C. final D. derived