Which of the following is not an example of user authentication?
A. Password
B. PINs
C. Fingerprint scanner
D. URLs (Uniform Resource Locators)
Answer: D
Computer Science & Information Technology
You might also like to view...
The layer functioning as the clipping mask is referred to as the ____.
A. mask layer B. clipped base C. base layer D. clipping layer
Computer Science & Information Technology
Dial-up computer networks, such as CompuServe, Prodigy, and America Online, typically charged some combination of monthly fee and hourly access fee
Indicate whether the statement is true or false
Computer Science & Information Technology
The statement numAddr = # stores the address that corresponds to the variable num in the variable numAddr.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology
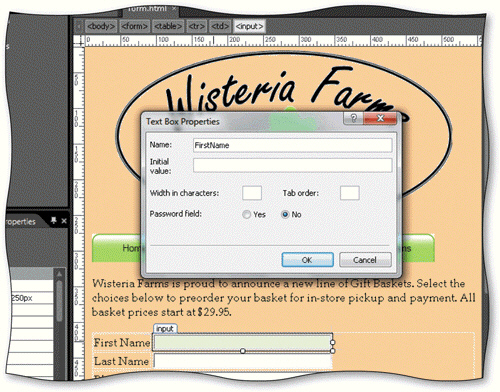 Using the accompanying figure as your guide, briefly list the steps to assign properties to a text box control.
Using the accompanying figure as your guide, briefly list the steps to assign properties to a text box control.
What will be an ideal response?
Computer Science & Information Technology