Methods in a class that do not provide implementations must be declared using keyword _________.
Fill in the blank(s) with the appropriate word(s).
abstract
You might also like to view...
When deriving a class from a protected base class, the public members of the base class become _________ and the protected members of the base class become __________?
a. protected, private b. public, private c. protected, protected d. public, protected
Which of the following statements about animation is NOT true?
A) An animation can be used to add a special visual effect. B) An animation can be assigned only to objects. C) Animation is any type of motion or movement that occurs in a presentation. D) Animation can be used to add sound effects to a presentation.
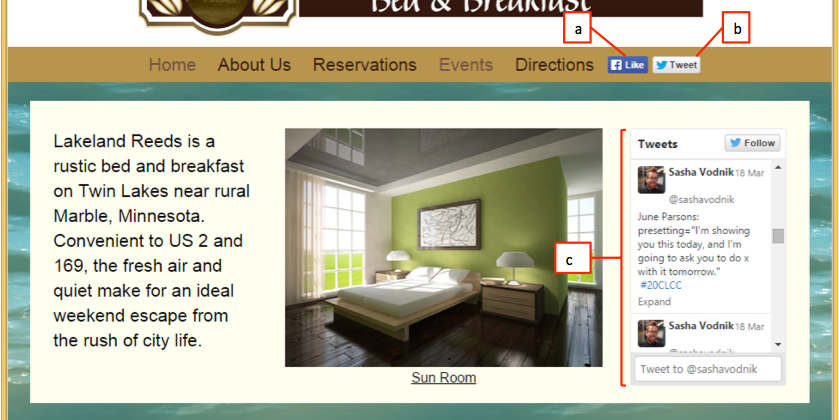
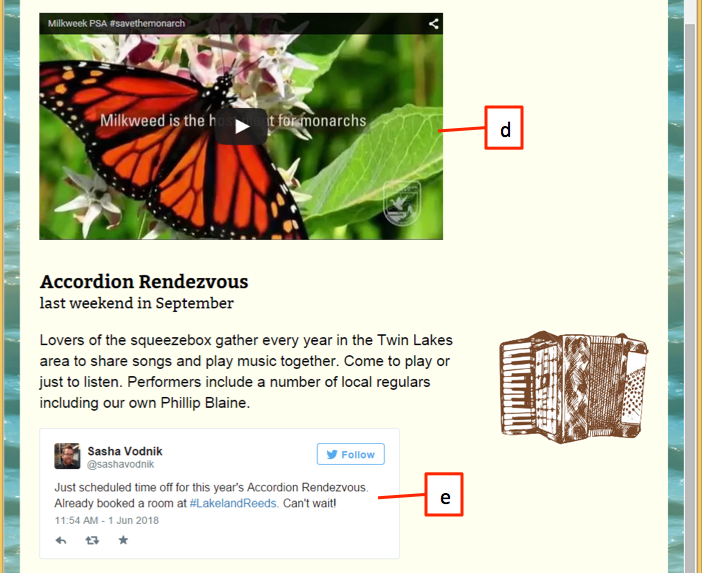
A. embedded video B. Facebook Like button C. embedded Instagram image D. Twitter feed
Used to collect personal information and transmits the information over the Internet to web-hosting sites. An example is a keylogger, which tracks the keys struck on a keyboard with the intent to steal someone's identity, credit card numbers, Social Security number, bank information, passwords, email addresses, and so forth.
What will be an ideal response?