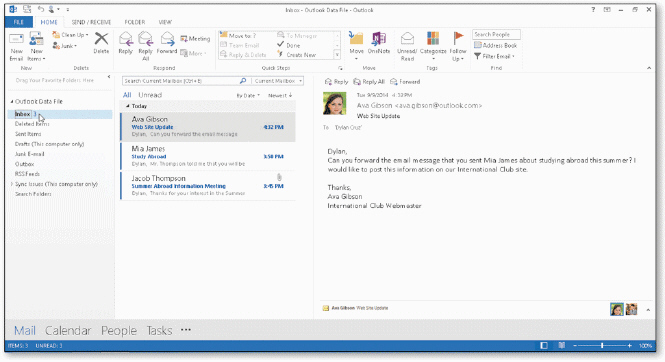
 As shown in the accompanying figure, the ____ accesses information that the Outlook Social Connector displays from social networks.
As shown in the accompanying figure, the ____ accesses information that the Outlook Social Connector displays from social networks.
A. People Pane
B. Navigation Pane
C. message pane
D. Reading Pane
Answer: A
You might also like to view...
Which of these does not focus on the relationship between the system analyst and the user with respect to output?
A) removal of all sources of bias from all output B) creating flexible output C) interactive design D) informing those concerned with output's biases
Find the error in the code segments, and explain how to correct it:
The following code should print the values 1 to 10: ``` n = 1; while (n < 10) { System.out.println(n++); } ```
Which type of backup would be best suited for a mission-critical system that modifies a small number of files between backups?
a) frequent physical backup b) infrequent logical backup c) frequent incremental backup d) infrequent incremental backup
____________________ hardening involves updating or patching applications as required, as well as properly administering usernames and passwords (changing default usernames and passwords).
Fill in the blank(s) with the appropriate word(s).