In the Needham and Shroeder authentication protocol with secret keys, explain why the following version of message 5 is not secure:
![]()
The purpose of message 5 is for A to convince B that 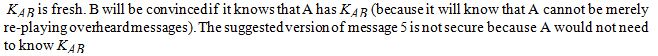 in order to send it, it could be sent by copying message 4.
in order to send it, it could be sent by copying message 4.
You might also like to view...
With the growing popularity of tablet computing and increasingly powerful smartphones, mobile computing has experienced moderate growth
Indicate whether the statement is true or false
To open a saved database, a user needs to start Access and click on Open Other Files, then click on the ________ button to locate the saved database
A) File B) Fill C) Home D) Browse
The Width and Height spin boxes located on the Picture Tools tab can be used to size a graphic proportionally
Indicate whether the statement is true or false
When using Solver, which of the following will NOT be identified during the process?
A) decision variable cells B) result cells C) constraint cells D) objective cells