Explain two practical guidelines to follow in risk treatment strategy selection.
What will be an ideal response?
- When a vulnerability (flaw or weakness) exists: Implement security controls to reduce the likelihood of a vulnerability being exploited.- When a vulnerability can be exploited: Apply layered protections, architectural designs, and administrative controls to minimize the risk or prevent the occurrence of an attack.- When the attacker's potential gain is greater than the costs of attack: Apply protections to increase the attacker's cost or reduce the attacker's gain by using technical or managerial controls.- When the potential loss is substantial: Apply design principles, architectural designs, and technical and non-technical protections to limit the extent of the attack, thereby reducing the potential for loss.
You might also like to view...
The __________ payload contains either error or status information associated with this SA or this SA negotiation.
A) Encrypted B) Notify C) Configuration D) Nonce
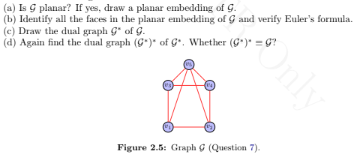
Consider the graph G shown in Figure 2.47 (reproduced in this document as Figure 2.5). Answer the following.
The Turing test is used to determine if a machine exhibits behavior indistinguishable from __________.
A. another machine B. a human C. an insect D. a rodent
Storing data in a list box whose ________ property is set to True is an easy way to organize the data contained in a sequential access file.
A. Alpha B. Grouped C. Sorted D. Ordered