Which of the following statements describes a legitimate source of the malicious data?
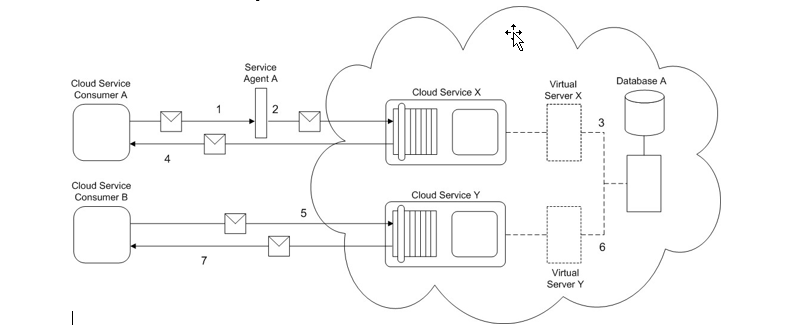
Cloud Service Consumer A sends a message to Cloud Service X (1), but it is first intercepted by Service Agent A (2) before actually being forwarded to Cloud Service X. Cloud Service X is hosted on Virtual Server X. Whenever an IT resource on Virtual Server X is accessed, the physical server that hosts Virtual Server X writes a log entry into Database A. After processing the request, Cloud Service X replies to Service Consumer A with a response message (4).
Cloud Service Consumer B sends a message to Cloud Service Y (5), which is hosted by Virtual Server Y. This virtual server is hosted by the same physical server as Virtual Server X and therefore when Cloud Service Y is accessed, a log entry is again written into Database A (6). After processing the request, Cloud Service X replies to Service Consumer A with a response message (7).
After being in use for several weeks, Cloud Service Consumer B unexpectedly shuts down. An investigation reveals that a response message sent by Cloud Service Y contained malicious data that
a. The source of the malicious data was Service Agent A. Upon intercepting the message from Cloud Service Consumer A, the service agent altered its contents prior to forwarding the message to Cloud Service X. Because Cloud Service X and Cloud Service Y share the same underlying physical server, this data compromised IT resources on that physical server which further compromised Virtual Server Y and Cloud Service Y.
c. The source of the malicious data was Cloud Service Consumer A. This program forwarded malicious data in the message it sent to Cloud Service X. Because Cloud Service X and Cloud Service Y share the same underlying physical server, this data compromised IT resources on that physical server that further compromised Virtual Server Y and Cloud Service Y
d. The source of the malicious data was Virtual Server Y. This virtual server was independently attacked. The attacker managed to place malicious software on the virtual server which inserted malicious data into the message sent by Cloud Service Y to Cloud Service Consumer B.
You might also like to view...
To delete a row, first click _____.
A. any cell in the row B. only the first cell in the row C. only the cell letter D. none of the above
One of the below programs that when called like this (with the underscore representing a digit from 1 to 4) generates this output:
``` >>> dup_("alphabet") ’_alphabetalphabetalphabetalphabetalphabetalphabetalphabetalphabet’ ```
Which of the following is NOT true about text files?
A) Text files are larger than XML files. B) Text files contain formatting. C) Text files do not contain graphics. D) Text files are also called ASCII files.
The tab on which page setup commands are found is:
a. File b. Layout c. Review