Let the function 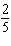 . Find
. Find 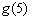 .
.
A. ![]() =
= ![]()
B. ![]() =
= ![]()
C. ![]() =
= ![]()
D. ![]() =
= ![]()
E. ![]() =
= ![]()
Answer: C
Computer Science & Information Technology
You might also like to view...
Which of the following best defines what signatures are?
a. IP addresses of known hackers. b. The email address of known attackers. c. Indicators of known attacks. d. None of these answers is correct.
Computer Science & Information Technology
A ________ is a predefined document structure that defines basic document settings, such as font, margins, and available styles
A) pattern B) template C) style D) theme
Computer Science & Information Technology
To play an audio track from the Library, ____ the track you want to play.
A. click B. double-click C. right-click D. hover over
Computer Science & Information Technology
A(n) ____________________ is an additional copy of a file or message that you store for safekeeping.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology