Match the computer crimes on the left with the crime descriptions on the right
1. Computer-assisted crime a. occurs due to the fact that computers are so widely used in today's world
2. Computer-targeted crime b. when a computer is used as a tool to help commit a crime
3. Incidental computer crime c. when a computer is the victim of an attack that's sole purpose is to harm the computer and its owner
4. Computer prevalence crime d. when a computer is involved in a computer crime without being the victim of the attack or the attacker
1-b, 2-c, 3-d, 4-a
You might also like to view...
In a database, ________ occurs when data is repeated multiple times
Fill in the blank(s) with correct word
The only use of the acceptance strategy that is recognized as valid by industry practices occurs when the organization has done all but which of the following?
A. determined the level of risk posed to the information asset B. performed a thorough cost-benefit analysis C. determined that the costs to control the risk to an information asset are much lower than the benefit gained from the information asset D. assessed the probability of attack and the likelihood of a successful exploitation of a vulnerability
What is the difference between the functions of an IDS and an IPS?
A An IDS will stop attacks, while an IPS will record details about violations. B An IDS will interrupt a communication, while an IPS will notify an administrator. C An IDS notice violations once they are occurring, while an IPS attempts to stop a violation from being successful. D An IDS is a software solution, while an IPS is a hardware appliance.
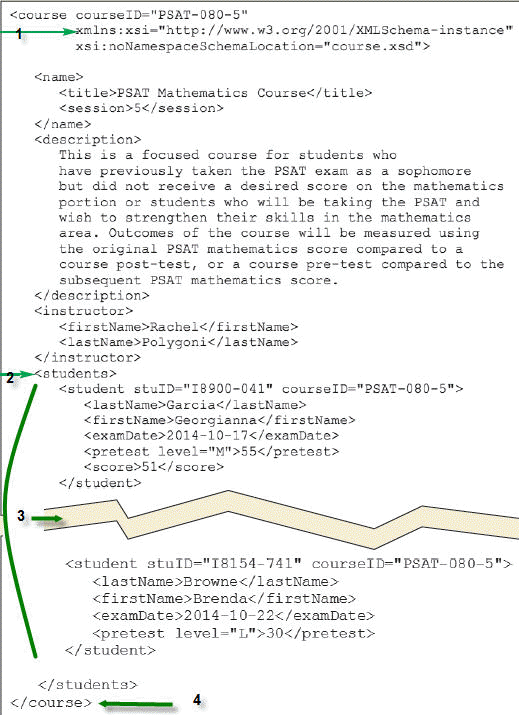
A. 1 B. 2 C. 3 D. 4