A scheme perpetrated over the Internet or by email that tricks a victim into voluntarily and knowingly giving money or property to a person is ________.
a. phishing
b. computer fraud
c. cyberterrorism
d. a botnet
b. computer fraud
You might also like to view...
Write a method to keep just the blue color. This means to set all the green and red values to zero.
What will be an ideal response?
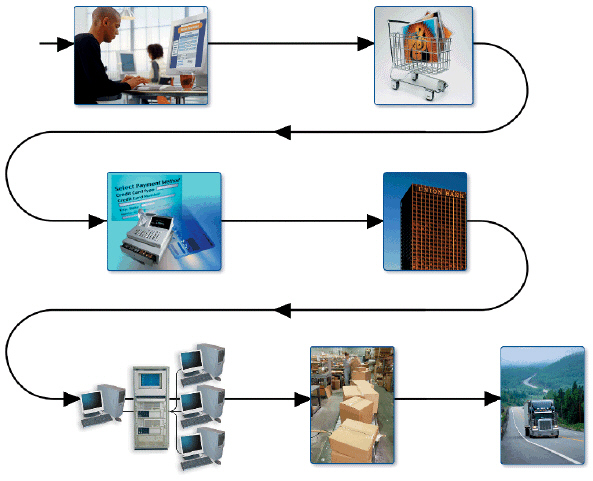 The final step in processing an online sales order is processing the customer's payment, as illustrated in the accompanying figure.
The final step in processing an online sales order is processing the customer's payment, as illustrated in the accompanying figure.
Answer the following statement true (T) or false (F)
Starting a computer when it is powered off is called a warm boot.
Answer the following statement true (T) or false (F)
Consider the following function to calculate the nth Fibonacci number:long fib (long num){ if (num == 0 || num == 1) return num; return (fib (num - 1) + fib (num - 2));}What is(are) the base case(s)?
A. 0 B. 1 C. 0 and 1 D. num - 1