The ___________ is where the organization housing its primary servers.
a. MDF
b. guest house
c. SOHO network
d. data center
e. load balancer
Ans: d. data center
Computer Science & Information Technology
You might also like to view...
From an application and system security standpoint, it is vitally important to ensure that every activity and task within the assurance process can be related to an ____.
A. established policy B. expected result C. indirect result D. observed result
Computer Science & Information Technology
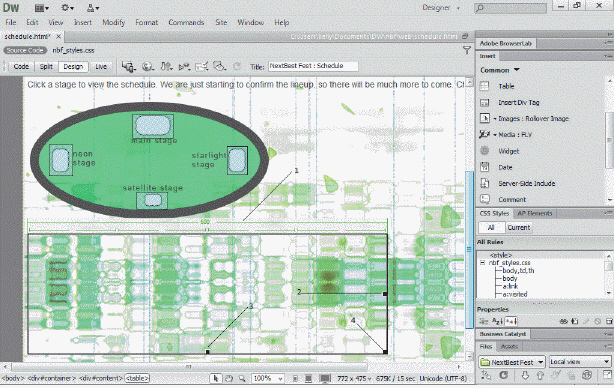 The item marked ____ in the accompanying figure is dragged to change table height.
The item marked ____ in the accompanying figure is dragged to change table height.
A. 1 B. 2 C. 3 D. 4
Computer Science & Information Technology
Computer forensics examiners have two roles: fact witness and ____ witness.
A. professional B. direct C. discovery D. expert
Computer Science & Information Technology
If a company invests in an intrusion detection system (IDS), other security controls will be unnecessary.
a. true b. false
Computer Science & Information Technology