Provide the Step on how Capture and Analyze ICMP Data in Wireshark
In this part, you will ping between two hosts in the Mininet and capture ICMP requests and replies in
Wireshark. You will also look inside the captured PDUs for specific information. This analysis should
help to clarify how packet headers are used to transport data to the destination.
Step 1. Examine the captured data on the same LAN.
In this step, you will examine the data that was generated by the ping requests of your team
member’s PC. Wireshark data is displayed in three sections: 1) The top section displays
the list of PDU frames captured with a summary of the IP packet information listed, 2) the
middle section lists PDU information for the frame selected in the top part of the screen and
separates a captured PDU frame by its protocol layers, and 3) the bottom section displays
the raw data of each layer. The raw data is displayed in both hexadecimal and decimal form.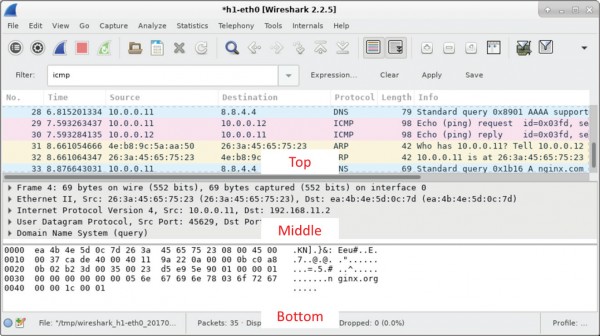
a. On Node: H1, enter wireshark-gtk & to start Wireshark (The pop-up warning is not
important for this lab.) Click OK to continue.
```
[root@secOps]# wireshark-gtk &
[1] 1552
[root@secOps ~]#
```
b. In the Wireshark window, under the Capture heading, select the H1-eth0 interface.
Click Start to capture the data traffic.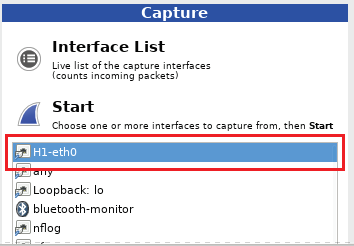
c. On Node: H1, press the Enter key, if necessary, to get a prompt. Then type ping -c 5
10.0.0.12 to ping H2 five times. The command option -c specifies the count or number
of pings. The 5 specifies that five pings should be sent. The pings will all be successful.
```
[root@secOps analyst]# ping -c 5 10.0.0.12
```
d. Navigate to the Wireshark window, click Stop to stop the packet capture.
e. A filter can be applied to display only the interested traffic.
Type icmp in the Filter field and click Apply.
f. If necessary, click the first ICMP request PDU frames in the top section of Wireshark.
Notice that the Source column has H1’s IP address, and the Destination column has
H2’s IP address.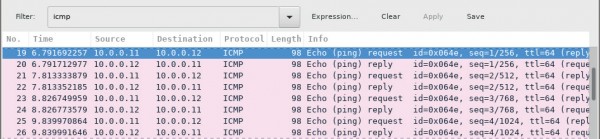
g. With this PDU frame still selected in the top section, navigate to the middle section.
Click the arrow to the left of the Ethernet II row to view the Destination and Source
MAC addresses.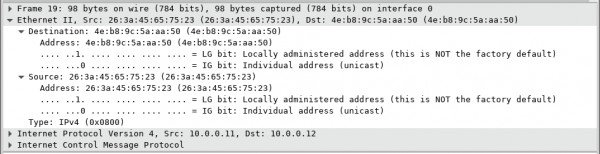
Does the Source MAC address match H1’s interface? ______ Yes
Does the Destination MAC address in Wireshark match H2’s MAC address? _____ Yes
STEP 2: Examine the captured data on the remote LAN.
You will ping remote hosts (hosts not on the LAN) and examine the generated data from
those pings. You will then determine what is different about this data from the data examined
in Part 1.
a. At the mininet prompt, start terminal windows on hosts H4 and R1.
```
mininet> xterm H4
mininet> xterm R1
```
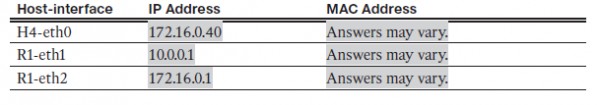
B. At the prompt on Node: H4, enter ifconfig to verify the IPv4 address and record the
MAC address. Do the same for the Node: R1.
```
[root@secOps analyst]# ifconfig
```
c. Start a new Wireshark capture on H1 by selecting Capture > Start. You can also click
the Start button or type Ctrl-E Click Continue without Saving to start a new capture.
d. H4 is a simulated remote server. Ping H4 from H1. The ping should be successful.
```
[root@secOps analyst]# ping -c 5 172.16.0.40
```
Review the captured data in Wireshark. Examine the IP and MAC addresses that you
pinged. Notice that the MAC address is for the R1-eth1 interface. List the destination IP
and MAC addresses.
IP: MAC:
IP addresses: 172.16.0.40. MAC address: This will be associated with the R1-eth1 interface,
which is the default gateway for the hosts H1, H2, and H3 in this LAN.
f. In the main CyberOps VM window, enter quit to stop Mininet.
```
mininet> quit
*** Stopping 0 controllers
*** Stopping 4 terms
*** Stopping 5 links
.....
*** Stopping 1 switches
s1
*** Stopping 5 hosts
H1 H2 H3 H4 R1
*** Done
```
g. To clean up all the processes that were used by Mininet, enter the sudo mn -c command
```
at the prompt.
analyst@secOps ~]$ sudo mn -c
[sudo] password for analyst:
*** Removing excess controllers/ofprotocols/ofdatapaths/pings/noxes
killall controller ofprotocol ofdatapath ping nox_core lt-nox_core ovs-openflowd
ovs-controller udpbwtest mnexec ivs 2> /dev/null
killall -9 controller ofprotocol ofdatapath ping nox_core lt-nox_core ovs-openflowd
ovs-controller udpbwtest mnexec ivs 2> /dev/null
pkill -9 -f "sudo mnexec"
*** Removing junk from /tmp
rm -f /tmp/vconn* /tmp/vlogs* /tmp/*.out /tmp/*.log
*** Removing old X11 tunnels
*** Removing excess kernel datapaths
ps ax | egrep -o 'dp[0-9]+' | sed 's/dp/nl:/'
*** Removing OVS datapaths
ovs-vsctl --timeout=1 list-br
ovs-vsctl --timeout=1 list-br
*** Removing all links of the pattern foo-ethX
ip link show | egrep -o '([-_.[:alnum:]]+-eth[[:digit:]]+)'
ip link show
*** Killing stale mininet node processes
pkill -9 -f mininet:
*** Shutting down stale tunnels
pkill -9 -f Tunnel=Ethernet
pkill -9 -f .ssh/mn
rm -f ~/.ssh/mn/*
*** Cleanup complete.
```
You might also like to view...
An array which has memory space set aside for it at compile time is a:
A. heap array B. static array C. dynamic array D. circular array
Design a data entry screen for entering new members.
What will be an ideal response?
In a query, the <> operator means not equal.
Answer the following statement true (T) or false (F)
The
Fill in the blank(s) with the appropriate word(s).