____________________ are found most often at checkout counters to record signatures used to authorize credit card purchases electronically.
Fill in the blank(s) with the appropriate word(s).
Signature capture devices
Computer Science & Information Technology
You might also like to view...
Case-based Critical Thinking QuestionsCase 14-2Urma has begun to apply the basic information that you have given her about schemas, and she to understand a schema with and without qualified XML Schema object names.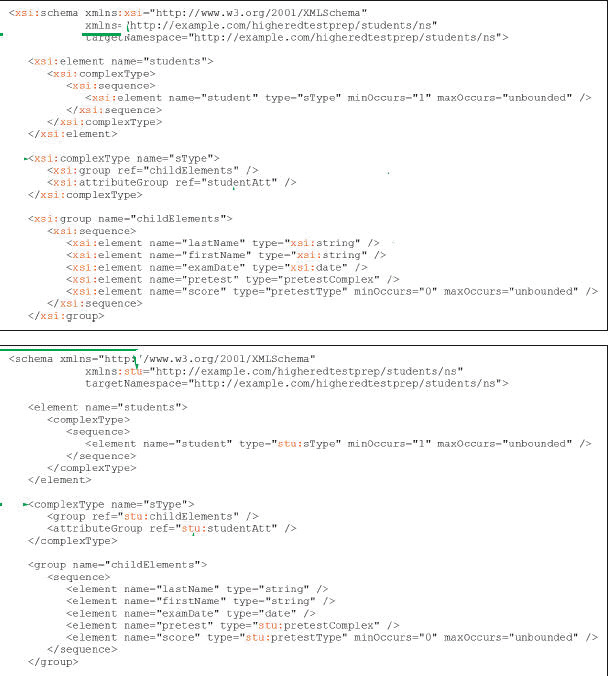 In the example code,
In the example code,
A. studentAtt B. ref C. stu:studentAtt D. stu
Computer Science & Information Technology
What are the tasks you can perform with the Security Configuration and Analysis tool?
What will be an ideal response?
Computer Science & Information Technology
A(n) _________ query removes records from a table when the query is run
Fill in the blank(s) with correct word
Computer Science & Information Technology
Where can time remapping be done?
What will be an ideal response?
Computer Science & Information Technology