Naming a table carefully is very important because it is the only way to describe what data that table contains
Indicate whether the statement is true or false
FALSE
Computer Science & Information Technology
You might also like to view...
The Calendar is the Outlook folder that contains your personal schedule of ____.
A. appointments B. events C. agendas D. meetings
Computer Science & Information Technology
The first password hacks were a response to the ___________________________________, developed in the early 1960s and first loaded on an IBM mainframe at MIT.?
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
A ____ is a predefined procedure that you can call (or invoke) when needed.
A. sub section B. sub code C. sub procedure D. method
Computer Science & Information Technology
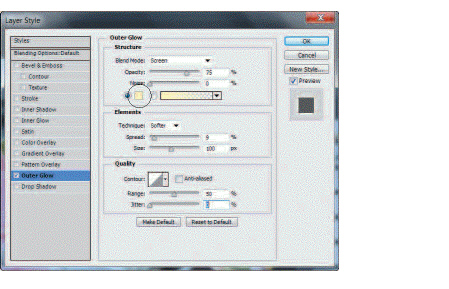 In the accompanying figure, the ____ determines the lighting angle at which the effect is applied to the layer.
In the accompanying figure, the ____ determines the lighting angle at which the effect is applied to the layer.
A. spread B. angle C. size D. distance
Computer Science & Information Technology