When emergency changes have to be made to systems, the system software may have to be modified before changes to the requirements have been approved. Suggest a model of a process for making these modifications that will ensure that the requirements document and the system implementation do not become inconsistent.
What will be an ideal response?
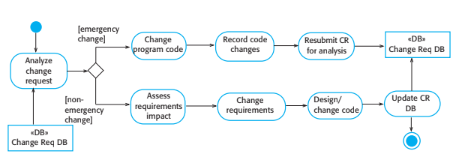
The following diagram shows a change process that may be used to maintain
consistency between the requirements document and the system. The process
should assign a priority to changes so that emergency changes are made but these
changes should then be given priority when it comes to making modifications to
the system requirements. The changed code should be an input to the final change
process but it may be the case that a better way of making the change can be found
when more time is available for analysis.
You might also like to view...
A JavaFX Button’s event handler receives a(n) ________, which indicates that the Button was clicked.
a. ButtonEvent b. ObjectEvent c. ControlEvent d. ActionEvent
By balancing information security and access, a completely secure information system can be created.
Answer the following statement true (T) or false (F)
A macro ________ creates a macro by recording the steps you perform in a routine activity
Fill in the blank(s) with the appropriate word(s).
A one-way connection created between two nodes communicating with IP Sec is known as ______________________
Fill in the blank(s) with the appropriate word(s).