A simpler version of the distributed garbage collection algorithm just invokes addRef at the site where a remote object lives whenever a proxy is created and removeRef whenever a proxy is deleted. Outline all the possible effects of communication and process failures on the algorithm. Suggest how to overcome each of these effects, but without using leases.
What will be an ideal response?
AddRef message lost - the owning site doesn’t know about the client’s proxy and may delete the remote object when it is still needed. (The client does not allow for this failure).
RemoveRef message lost - the owning site doesn’t know the remote object has one less user. It may continue to keep the remote object when it is no longer needed.
Process holding a proxy crashes - owning site may continue to keep the remote object when it is no longer needed.
Site owning a remote object crashes. Will not affects garbage collection algorithm
When a removeRef fails, the client can repeat the call until either it succeeds or the owner’s failure has been detected.
One solution to a proxy holder crashing is for the owning sites to set failure detectors on holding sites and then remove holders after they are known to have failed.
You might also like to view...
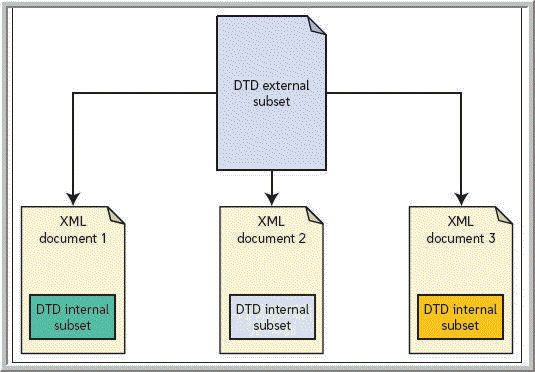 Which of the following is a type of identifier for the location of an external subset like the one in the accompanying figure?
Which of the following is a type of identifier for the location of an external subset like the one in the accompanying figure?
A. internal B. undeclared C. qualified D. system
When working in the Windows 10 CLI, the XCOPY command can be used with what switch to make the operating system not display filenames while copying?
A. /E B. /Q C. /S D. /V
Which of the following keyboard shortcut duplicates a selection from the original location and places it in the Clipboard?
A) Ctrl+X B) Ctrl+A C) Ctrl+C D) Ctrl+V
What statement regarding the Secure Socket Tunneling Protocol is NOT accurate?
A. SSTP is viewed as more secure that PPTP or L2TP because it encrypts using a 128-bit key. B. SSTP authenticates users with 2048-bit key certificates. C. SSTP encapsulates data packets in HTTP. D. SSTP uses Transport Layer Security for secure communications.