Show the hex addresses and variable values after the statements have been executed. (All pointers are 4 bytes!)
The first byte of memory below is xFF2A.
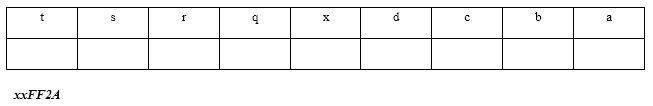
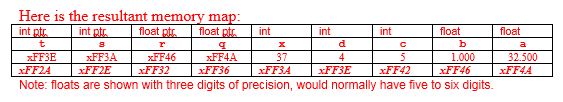
```
int main()
{
float a= 32.5, b;
int c = 5, d = 4.5, x;
float *q, *r;
int *s, *t;
q = &a;
r = &b;
s = &x;
t = &d;
*r = c%d;
*s = *t + c;
```
You might also like to view...
Administrative controls relating to the security of private keys can be employed by including a __________ (which includes date and time) and to require prompt reporting of compromised keys to a central authority.
Fill in the blank(s) with the appropriate word(s).
Configure the network according to the specifications listed in the previous section. Select the IP address for each networking device in each network segment.
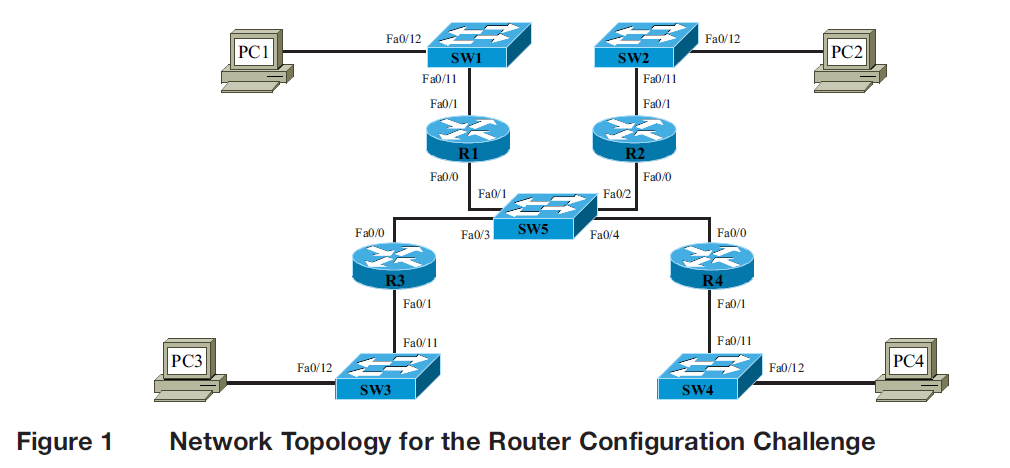
Test your network carefully, and then save your configuration. All machines should be able to ping
each other. You will be asked to verify that you have configured routing to all subnets in your network.
Be sure and save the configuration; you will be asked to demonstrate your network to your
instructor.
You can create a copy of a worksheet by pressing the ____ key as you drag and drop its sheet tab.
A. Ctrl B. Tab C. F3 D. Enter
To achieve defense in depth, an organization must establish multiple layers of security controls and safeguards.
Answer the following statement true (T) or false (F)