____ files involves combining two or more files while maintaining the sequential order of the records.
A. Merging
B. Sorting
C. Splitting
D. Dividing
Answer: A
You might also like to view...
Different sorting algorithms on a particular array produce the same result; the choice of algorithm affects ________ of the program that implements the algorithm.
a. only the run time b. the run time and the memory use c. only the memory use d. neither the run time nor the memory use
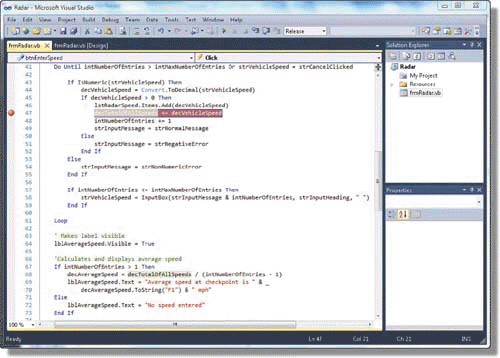 As shown in the accompanying figure, ____ are stop points placed in the code to tell Visual Studio 2010 debugger where and when to pause the execution of the program.
As shown in the accompanying figure, ____ are stop points placed in the code to tell Visual Studio 2010 debugger where and when to pause the execution of the program.
A. breakpoints B. debug points C. halt points D. tracepoints
To copy attributes to more than one object or section of text, select the object whose attributes you want to copy, double-click the Paste icon, and then click each of the objects or sections of text you want to format.
Answer the following statement true (T) or false (F)
Match each item with a statement below.
A. A modem from which communications occur in discrete units, and in which the start of a unit is signaled by a start bit at the front, and a stop bit at the back signals the end of the unit. B. An encrypted handshake protocol designed for standard IP- or PPP-based exchange of passwords. It provides a reasonably secure, standard, cross-platform method for sender and receiver to negotiate a connection. C. A technology that uses advanced modulation techniques on regular telephone lines for high-speed networking at speeds of up to about 52 Mbps between subscribers and a telecommunications company. D. Consists of guidelines for negotiating authentication methods, 40 methods having been defined by the time of this writing, including for wired and wireless authentication methods. E. A WAN communications technology that relies on packet switching and virtual connection techniques to transmit at rates from 56 Kbps to 45 Mbps. F. A protocol that establishes security associations, including cryptographic keys, for IPsec secured communications. G. A protocol that transports PPP over a VPN, an intranet, or the Internet. Similar to PPTP, it uses an additional network communications standard called Layer Two Forwarding. H. An enhancement of MS-CHAP that provides better authentication and data encryption and that is especially adapted for VPNs. I. A capability of a remote access server to aggregate multiple data streams into one logical network connection for the purpose of using more than one modem, ISDN channel, or other communications line in a single logical connection. J. A modem that communicates using continuous bursts of data controlled by a clock signal that starts each burst.