The most popular background color is _____.
A. blue
B. white
C. red
D. yellow
Answer: A
You might also like to view...
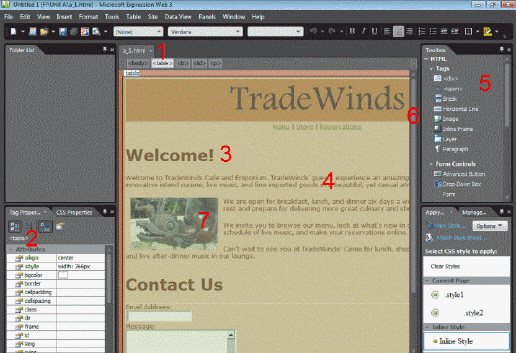 Referring to the figure above, which number indicates the table tag selected in the quick tag selector bar?
Referring to the figure above, which number indicates the table tag selected in the quick tag selector bar?
A. 1 B. 2 C. 4 D. 5
Match each item with a statement below.
A. A technique used by hypervisors to cause a guest VM to release infrequently used memory pages. B. A networking mode that allows traffic from a virtual machine to pass through unchanged to the physical network as though it were directly attached. C. A virtual disk file that allocates space on the hosting hardware only as it is required to satisfy the needs of the guest VM. D. Used to create additional logical cores that can be used by the hypervisor to improve the performance of virtual machines. E. A piece of software that enables the sharing of hardware resources between the hosting operating system and virtual environments. F. A method of separately storing any changes to a parent VM made by a specific user such that it does not affect the parent VM. G. A standard created by industry wide vendors in various areas of virtualization for the purpose of copying or moving virtual machines between different platforms. H. An accumulation of specialized and departmental servers that increases costs of computer hardware and maintenance, as well as power consumption. I. A personal computer that runs its own operating system and applications. J. A software package that includes a virtual machine containing a preinstalled and configured application that's ready to use.
Security testers and hackers use which of the following to determine the services running on a host and the vulnerabilities associated with these services?
a. Zone transfers b. Zone scanning c. Encryption algorithms d. Port scanning
What specific internal control procedure would prevent the sale of goods on account to a fictitious customer?
What will be an ideal response?