A ____ is also an identifier consisting of an IP address and port number, such as 172.16.0.1:80.
A. socket
B. route
C. domain name
D. URL
Answer: A
Computer Science & Information Technology
You might also like to view...
Which of the following is true about encryption algorithms?
A. their strength is tied to their key length B. not vulnerable to brute force attacks C. block ciphers encrypt one bit at a time D. asymmetric algorithms use a single key
Computer Science & Information Technology
In the accompanying figure, box _____ denotes a sender composing an email.
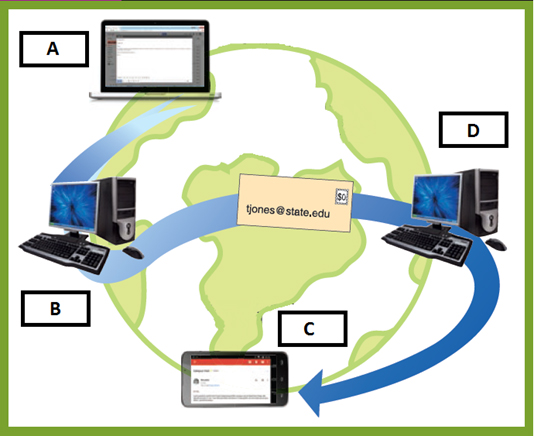
A. ?A B. ?B C. ?C D. ?D
Computer Science & Information Technology
An associative list is automatically maintained in a sorted order.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology
The technical term "____" refers to communications that occur outside of previously established communications method or channel.
A. real-time B. in-line C. in-band D. out-of-band
Computer Science & Information Technology