Unlike WEP the PSK is not used for encryption but instead serves as the starting point (____) for mathematically generating the encryption keys.
A. seed
B. per-packet key
C. MIC
D. CRC
Answer: A
You might also like to view...
Configure the network according to the specifications listed in the previous section. Select the IP address for each networking device in each network segment.
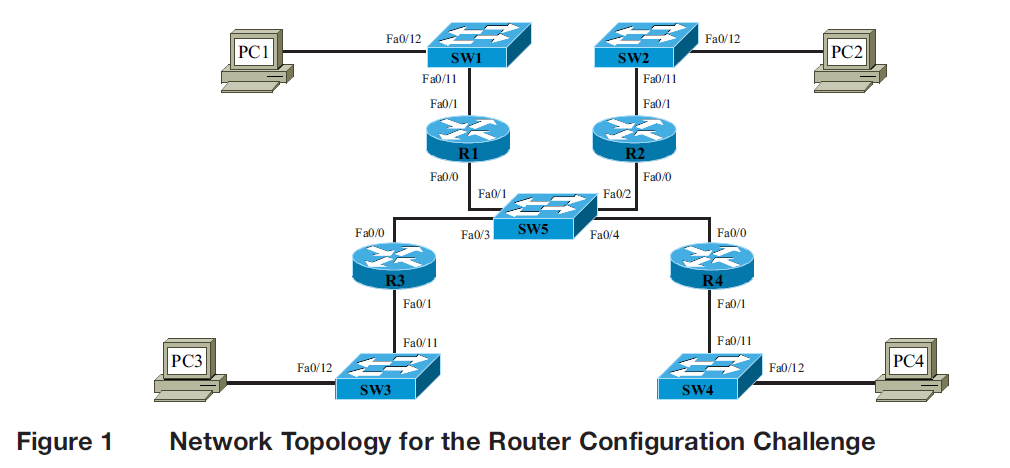
Test your network carefully, and then save your configuration. All machines should be able to ping
each other. You will be asked to verify that you have configured routing to all subnets in your network.
Be sure and save the configuration; you will be asked to demonstrate your network to your
instructor.
What would the browser output if the following script is executed?
```
< SCRIPT LANGUAGE = "JavaScript" >
var array = [ [ 1, 2, 3 ], [ 1, 2, 3 ] ];
for ( var i in array ) {
for ( var j in array[ i ] )
document.write( array[ i ][ j ] + " " );
document.writeln("
");
}
< /SCRIPT >
```
a) Nothing, the script would generate an error
b) 1 2 3
c) 1 2 3 4 5 6
d) 1 2 3 1 2 3
List the four guidelines for good display design.
What will be an ideal response?
What is the goal of event data analysis?
A. Locate new exploitations. B. Interpret collected events, and take appropriate action. C. Discover the identity of perpetrators. D. Reduce the vulnerabilities of an organization.