Which of the following is NOT a critical goal of information security?
A. confidentiality
B. scalability
C. authentication
D. nonrepudiation
Answer: B
You might also like to view...
Correct statements of similarities and differences between calling user defined functions and library functions are:
a) Similarity: A call to either requires the function name followed by parenthesized comma separated list of arguments that match the prototype in number and type.
b) Difference: Library functions require inclusion of header files for declarations but user defined functions do not require any declaration before use.
c) Similarity: Either library or user defined functions may be value returning or void functions.
d) Difference: Library functions all provide a return value, user functions must be void functions.
e) Difference Library function declarations (sometimes definitions) come from #include
The open-source descendant of Nessus is called which of the following?
A. NW B. WNessus C. OpenVAS D. WinNessus
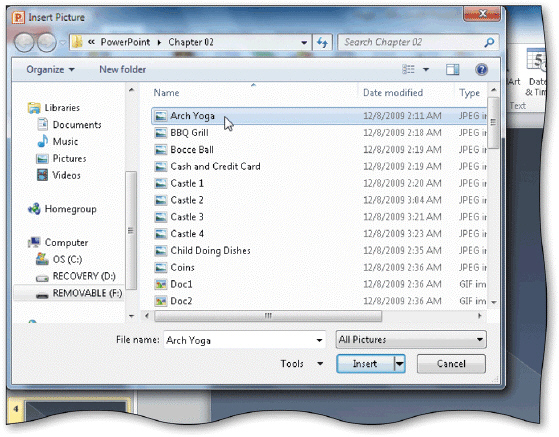 Clicking which of the following buttons opens the Insert Picture dialog box shown in the accompanying figure?
Clicking which of the following buttons opens the Insert Picture dialog box shown in the accompanying figure?
A. Clip Art B. Insert Picture from File C. Screenshot D. New Photo Album
A class of statistics students was asked to tell the number of miles each drove to school (one way). Use these numbers to construct a stem-and-leaf display of commuting distances. 6515122516124812212511101422931310829311216415121136
A. 
B. 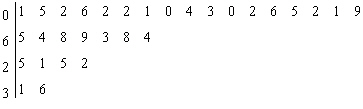
C. 
D. 
E. 