When a threat turns into a valid attack, it is classified as an information security incident, but only if it has certain characteristics. What are these characteristics?
What will be an ideal response?
It is directed against information assets owned or operated by the organization.
It has a realistic chance of success.
It threatens the confidentiality, integrity, or availability of information resources and assets.
Trades & Technology
You might also like to view...
____________________ is a form of sprigging
Fill in the blank(s) with correct word
Trades & Technology
31.45 ÷ 8.5 =
A) 4.8 B) 3.7 C) 4.7 D) 3.8
Trades & Technology
Discuss what types of errors could occur related to the dimensioning of drawings
What will be an ideal response?
Trades & Technology
Technician Asays the procedure illustrated is a method of seating new pads. Technician B says the procedure illustrated shows checking for a seized caliper piston by attempting to retract it. Who is correct?
?
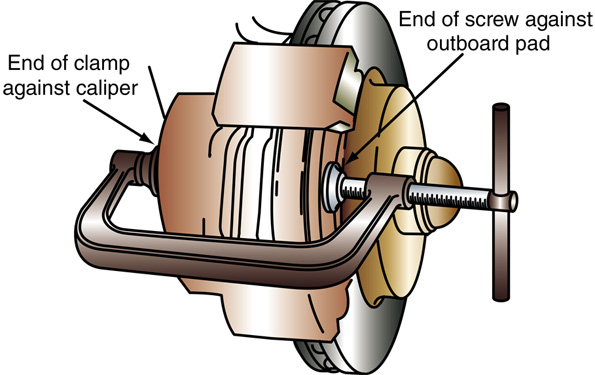
A. A only B. B only C. Both A and B D. Neither A nor B
Trades & Technology