Hacking to make a political statement is called ________.
A) politicking
B) sneaking
C) cracking
D) hacktivism
Answer: D) hacktivism
Computer Science & Information Technology
You might also like to view...
Computers process data under the control of sets of instructions called computer _______ .
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
You can select nonadjacent ranges using the SHIFT key.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology
Which of the following Windows DHCP log file event IDs indicates that a lease request could not be satisfied because the scope's address pool was exhausted?
A. 01 B. 02 C. 10 D. 14
Computer Science & Information Technology
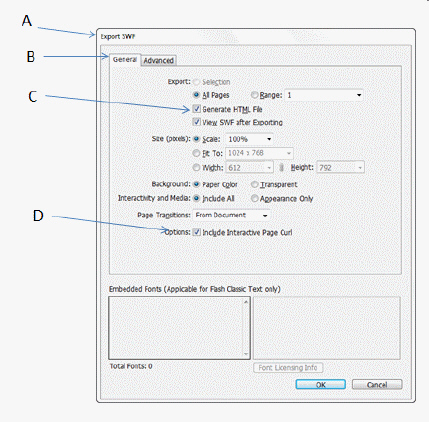 Item D in the accompanying figure shows the option that must be checked if want users to be able to drag a corner of a page in an SWF file.
Item D in the accompanying figure shows the option that must be checked if want users to be able to drag a corner of a page in an SWF file.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology