Prove Equation 8.14.
What will be an ideal response?
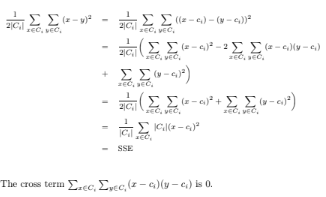
Computer Science & Information Technology
You might also like to view...
The protocol used to send most email messages is ________.
a. ICMP b. POP3 c. FTP d. SMTP
Computer Science & Information Technology
If a cell is locked, it does not matter whether protection is turned on or not.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology
You work in a company that accesses the Internet frequently. This makes the company's network vulnerable to attacks. You want to protect your company's network from external attacks. Which of the following will you use to accomplish the task?
A) Repeater B) DHCP relay agent C) Antivirus D) Firewall
Computer Science & Information Technology
The command to turn Smart Guides on and off can be found under which menu on the Menu bar?
A. File B. Edit C. Object D. View
Computer Science & Information Technology