The ____ tile displays a screen where you can work with multiple applications.
A. Search
B. Start
C. Desktop
D. Live
Answer: C
You might also like to view...
Configure the network according to the specifications listed. Make sure that you address both the internal and external access rules. Test your network carefully and then save your configuration. You will be asked to demonstrate your network to your instructor for grading. Make sure the ping command operates properly and the access rules are being implemented as specified in the requirements.
The objective of this project is for the students to gain experience configuring VLANs and access
lists for controlling data traffic into and out of the VLANs and the wide-area network connection.
This network setup has two separate sites, Site A and Site B, that are connected through Routers 1
and 2. The network address for Site A is 172.168.0.0. The network address for Site B is
192.168.35.0. IP addressing and subnetting within your network is up to you; however, plan your
network carefully.
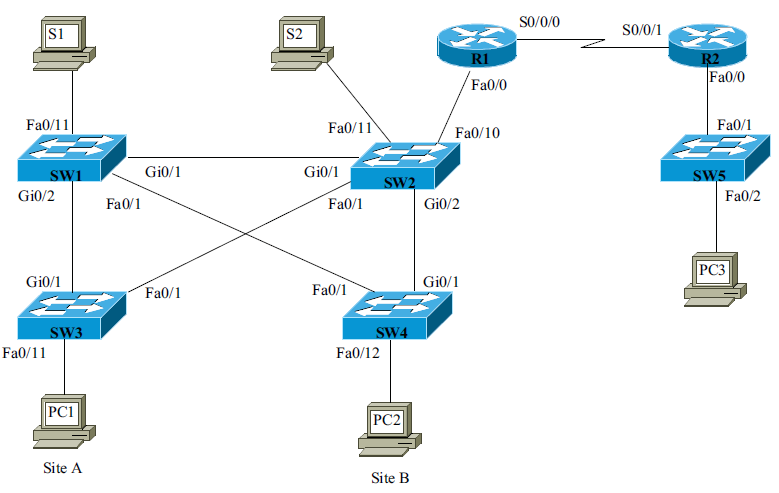
Specifics
Site A:
? Research VLAN (PC1), server (S1)
? Finance VLAN (PC2), server (S2)
Site B:
? Office LAN (PC3)
Internal access rules:
? Computers on the Office and Finance VLANs can communicate with the server (S2).
? Only the computers in the Research VLAN can talk to the Research server (S1).
External access rules:
? Only the computers in the Office and Finance LANs can access the wide-area network conne
Under HIPAA, if a patient wants his patient information released to a person or organization that is not a covered entity, this cannot happen
Indicate whether the statement is true or false
In Excel, you need to be a programmer to create macros.
Answer the following statement true (T) or false (F)
Alice sends a message to Bob and wants to ensure that Mal, a third party, does not read the contents of the message while in transit. What goal of cryptography is Alice attempting to achieve?
A. Confidentiality B. Integrity C. Authentication D. Nonrepudiation