Which of the following is commonly done as part of a vulnerability scan?
A. Exploiting misconfigured applications
B. Cracking employee passwords
C. Sending phishing emails to employees
D. Identifying unpatched workstations
Answer: C. Sending phishing emails to employees
You might also like to view...
What is wrong with the following code?
float scores[10], total; a. Cannot declare regular and array variables together. b. Arrays must be integers c. The 10 should be replaced with a variable name, whose value is input from the user d. Nothing.
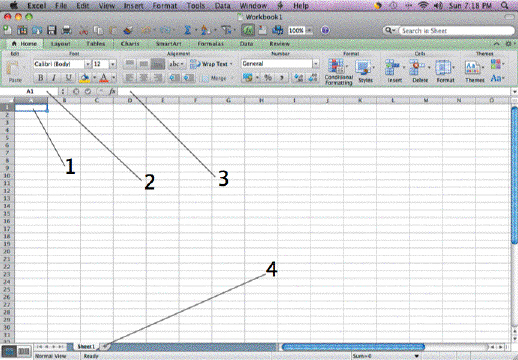 In the accompanying figure, Item 3 points to the ____.
In the accompanying figure, Item 3 points to the ____.
A. Name box B. title bar C. Formula bar D. toolbox
What manages the resources on a network?
A. client B. server C. Bluetooth D. modem
How can an administrator initiate a system state recovery using the command line?
A. wbadmin staterecovery start B. wbadmin start systemstaterecovery C. wbadmin recover D. wbadmin restore catalog