The ________is the high-level information security policy that sets the strategic direction, scope, and tone for all of an organization's security efforts.
A. SysSP
B. EISP
C. GSP
D. ISSP
Answer: B
You might also like to view...
A shape can be given an absolute position in a Canvas using the Canvas’s methods _____ and _____.
a) SetX, SetY b) SetLeft, SetTop c) PositionX, PositionY d) PadLeft, PadTop
Generally speaking, how does the file size change if the number of pixels of both the width and height of an image are doubled?
What will be an ideal response?
Case Based Critical Thinking QuestionsCase 17-1Maxwell has developed a Movies database. He presented his design to his class, and some of his listeners had questions.Here is one of the tables Maxwell showed to the audience.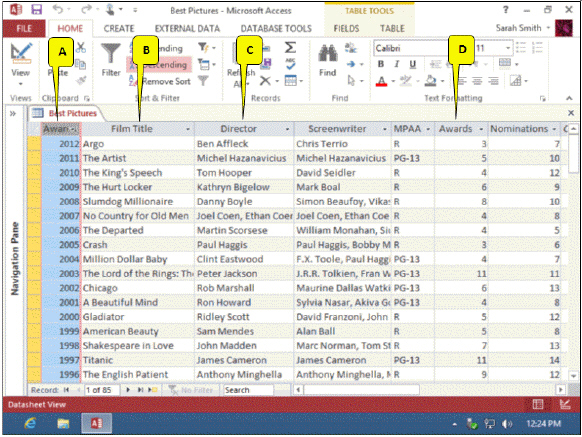 Referring to the accompanying figure, James asks which of the columns is a primary key. Maxwell points to _____.
Referring to the accompanying figure, James asks which of the columns is a primary key. Maxwell points to _____.
A. A B. B C. C D. D
When a dynamic DNS record is created, what is the TTL value used for?
A. To determine how many hops away the updating client is B. To specify the time before the next update C. To specify how long the record should remain in the DNS database D. To determine how long it takes for a ping to reach the client and come back