Which of the following is not an example of authentication by knowledge?
A) Cognitive password
B) PIN
C) One-time passcode
D) Password
C) One-time passcode
You might also like to view...
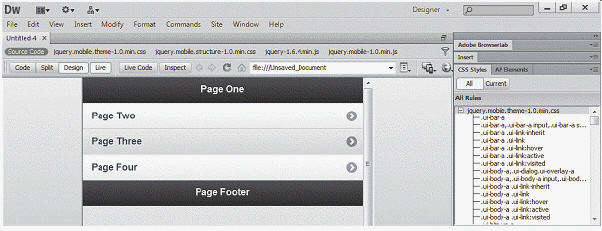 As shown in the accompanying figure, page elements ____________________ to fit in a window.
As shown in the accompanying figure, page elements ____________________ to fit in a window.
Fill in the blank(s) with the appropriate word(s).
Answer the following statements true (T) or false (F)
1. The last item entered onto a stack is the first item removed from that stack. 2. A queue is similar to a stack in that items are entered and removed in the same order. 3. When an array is used to implement a stack or a queue, the entire array is allocated at once, whether or not it is all needed. 4. Attempting to reference a list node after the node is returned to the heap causes the compiler to generate an error message. 5. When the operator new returns a zero pointer, it means that all of the cells on the heap have been allocated.
The ________ Print page allows the user to select a printer, indicate which pages to print, and to choose how many copies to print
Fill in the blank(s) with correct word
A technician needs to setup an Internet connection for a small office. There are five users that need the ability to use email and do online research. The office manager wants the connection to be always on and be as inexpensive as possible. Which of the following would BEST fit the needs of this office?
A. Broadband B. T1 C. Frame Relay D. Satellite