_________________________ occurs when a hacker takes control of a TCP session between two hosts.?
Fill in the blank(s) with the appropriate word(s).
TCP session hijacking
You might also like to view...
Session hijacking is a specialized form of ____ in which a hijacker gets unauthorized control of a network session.
A. ping flooding B. address spoofing C. denial-of-service (DoS) D. CGI scripting
h1 headings are the smallest text size, and h6 headings are the largest.
Answer the following statement true (T) or false (F)
A _ occurs when someone creates an entire network of zombie computers that the person controls without the knowledge of the user. The creator of the _ can then perform tasks, such as email spamming, on the infected computers.
Fill in the blank(s) with the appropriate word(s).
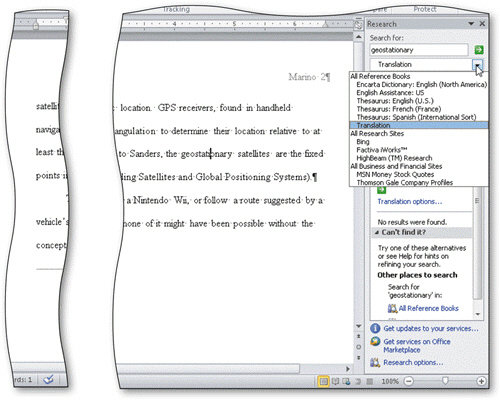 Some ____ available in the Research task pane, as shown in the accompanying figure, include a dictionary and, if you are connected to the Web, a search engine and other Web sites.
Some ____ available in the Research task pane, as shown in the accompanying figure, include a dictionary and, if you are connected to the Web, a search engine and other Web sites.
A. dialogs B. pathways C. indices D. services