Give an overview of the threats that come under the heading of "malware."
What will be an ideal response?
Malware includes a variety of programs or code that do something to your computer or network that you do not want to have occur. There are many varieties of malware. A short list includes viruses, worms, macros, Trojans, rootkits, adware, and spyware.
You might also like to view...
Answer the following statements true (T) or false (F)
1. If the string variable, name has the value "Anne.Smith", then the following statement would return annesmith. Set newName = toLower(name) 2. If the integer variable, number has the value 5, then the following statement would return 25 to result. Set result = sqrt(number) 3. Given an integer variable, number. The only possible values for number that could result from the following statement are 1 and 2. Set number = random(0, 2) 4. The following pseudocode would display Hello, friend. Declare String str1 = "Hello," Declare String str2 = " friend" Set message = append(str1, str2) Display message
Explain how Router1, in the previous example, knows that datagram destined to network 10.0.3.10 should be forwarded 10.0.2.2?
What will be an ideal response?
The operation create inserts a new bank account at a branch. The transactions T and U are defined as follows:
T: aBranch.create("Z");
U: z.deposit(10); z.deposit(20).
Assume that Z does not yet exist. Assume also that the deposit operation does nothing if the account given as argument does not exist. Consider the following interleaving of transactions T and U:
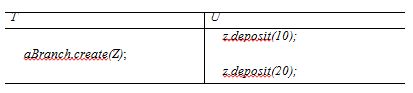
State the balance of Z after their execution in this order. Are these consistent with serially equivalent executions of T and U?
Exporting tables and queries to Excel is usually predictable and consistent because of the similarity between an Access datasheet and an Excel spreadsheet
Indicate whether the statement is true or false