Microsoft's STRIDE threat assessment framework uses six categories for threats: Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege. If a penetration tester is able to modify audit logs, what STRIDE categories best describe this issue?
A. Tampering and information disclosure
B. Elevation of privilege and tampering
C. Repudiation and denial of service
D. Repudiation and tampering
Answer: D. Repudiation and tampering
You might also like to view...
Get methods are commonly called ___________ or ___________ .
Fill in the blank(s) with the appropriate word(s).
?In the accompanying image of Microsoft Excel 2016, box A points to the _____.
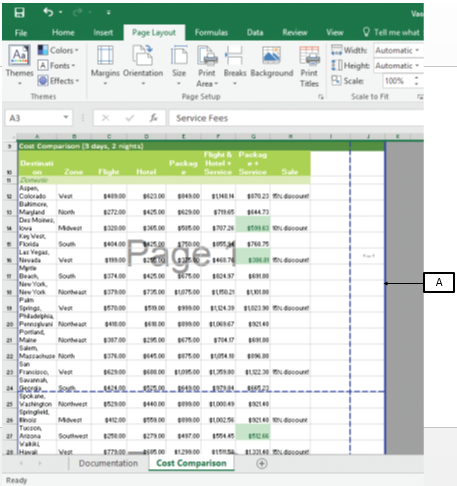
A. ?manual page break B. ?automatic page break C. ?worksheet border D. ?error indicator
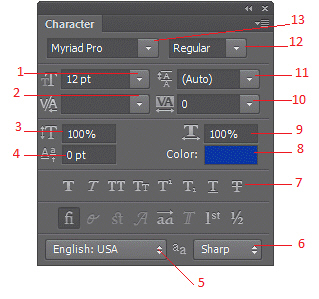 In the accompanying figure, item 9 points to the ____.
In the accompanying figure, item 9 points to the ____.
A. Vertical scale B. Horizontal scale C. Baseline shift D. Tracking
Taking the output of one method and using it as input for a subsequent method is accomplished through a process referred to as ____ the two methods together.
A. appending B. chaining C. binding D. linking