Which of the following is the preferred way of printing the data found in tables?
A) Form B) Query C) Table D) Report
D
You might also like to view...
The security specialist role is also responsible for establishing and routinely evaluating the effectiveness of the vendor management program.
Answer the following statement true (T) or false (F)
Within the /usr/share directory hierarchy, list the number of times the word 27 occurs in files in which it occurs at least once. Hint: Connect the output of one grep command to the input of another grep command using a pipe; the first grep command should display the count for all files in the hierarchy and the second should get rid of those with a count of 0.
What will be an ideal response?
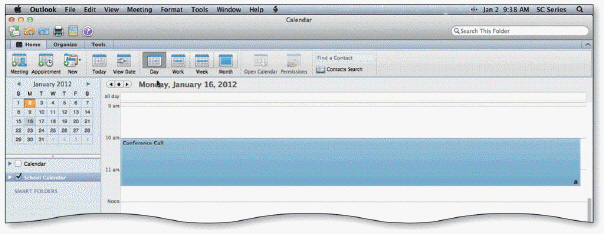 In the accompanying figure, the status of the appointment is Free.
In the accompanying figure, the status of the appointment is Free.
Answer the following statement true (T) or false (F)
A(n) ____ is one that does not run as a separate (stand-alone) program.
A. second-generation language B. scripting language C. first-generation language D. interpreted language