An internal virtual network allows virtual machines to access the physical network and communicate with physical servers and clients.
Answer the following statement true (T) or false (F)
False
Computer Science & Information Technology
You might also like to view...
____ are collections of IP addresses of known spam sources on the Internet, and they can be easily integrated into most SMTP server configurations.
A. Real-time blacklistings (RBLs) B. Cross-site scriptings C. SMTP traps D. Domain Name Security Extensions
Computer Science & Information Technology
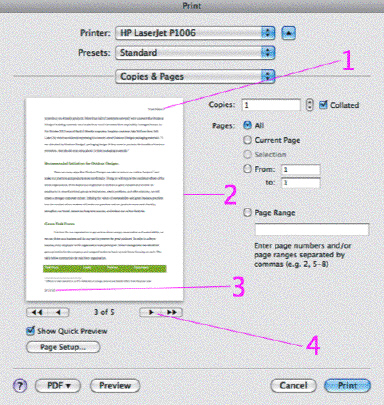 The accompanying figure illustrates a(n) ____ showing header and footer.
The accompanying figure illustrates a(n) ____ showing header and footer.
A. Outline View B. Print Layout View C. Full Screen View D. Quick Preview
Computer Science & Information Technology
Access lists to block a router's outward delivery must be applied as ____________________ filters.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
When you decrease the row height to _____, the row is hidden.
A. 0 B. 1 C. 2 D. 3
Computer Science & Information Technology