The payload is __________
A. a program that gives the attacker remote access control on a computer
B. a small program that, after installed, downloads a larger attack program
C. the code that does damage
D. a program that hides itself by deleting a system file and taking on the system file's name
C. the code that does damage
You might also like to view...
Many PivotChart elements can be formatted like those in other charts
Indicate whether the statement is true or false.
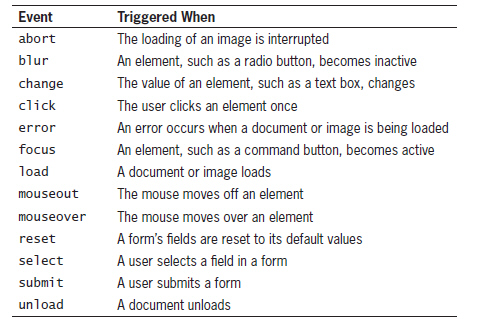 According to the accompanying table, when a user clicks a form button, a ____ event is generated.
According to the accompanying table, when a user clicks a form button, a ____ event is generated.
A. select B. change C. click D. submit
The ____ format produces a file consisting of all the Photoshop layers and also supports transparency.
a. TIFF b. JPEG c. PHP d. PDF
You can create a(n) ____ reference by deleting the $ from the row reference in the cell reference $B$6.
A. mixed B. absolute C. relative D. indexed