______ occur when a computer system is accessed without permission.
a. Distributed denial of services
b. Rogue access points
c. Micro-segments
d. Network intrusions
d. Network intrusions
Criminal Justice
You might also like to view...
List three higher risk activities that may make a college student more likely to be a victim of crime.
What will be an ideal response?
Criminal Justice
We are all "victims" of burglary
Indicate whether the statement is true or false
Criminal Justice
Complete the following table:
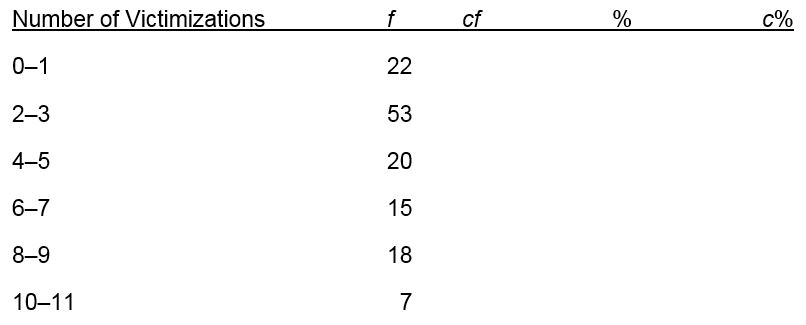
What will be an ideal response?
Criminal Justice
A __________ is used to enumerate a department's purpose
Fill in the blank(s) with correct word
Criminal Justice