The overall scheme of Kerberos is that of a trusted third party authentication service that uses a protocol based on a proposal by __________ .
A. Needham and Schroeder
B. Kehn
C. Denning
D. Gong
A. Needham and Schroeder
Computer Science & Information Technology
You might also like to view...
The ____________ is a method that returns the property's value.
a. Me method b. get accessor c. Show method d. this.Value method
Computer Science & Information Technology
Answer the following questions true (T) or false (F)
1. The for statement, do…while statement and while statement are examples of branching mechanisms. 2. When choosing a sentinel value, you should choose a value that would never be encountered in the input of the program.
Computer Science & Information Technology
The ________ are the commands in the left panel of Backstage view
Fill in the blank(s) with correct word
Computer Science & Information Technology
A computer runs an instruction set with the following characteristics
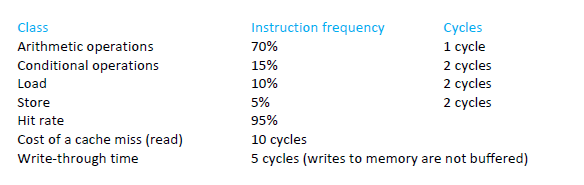
What is the average number of cycles per instruction?
Computer Science & Information Technology