Use caution when assigning a shortcut key to a macro so you do NOT override an existing shortcut within Excel
Indicate whether the statement is true or false
TRUE
You might also like to view...
c. sort(begin(values), end(values));
a. A nonconstant pointer to nonconstant data. b. A nonconstant pointer to constant data. c. A constant pointer to nonconstant data. d. A constant pointer to constant data.
An alternative approach to the key-exchange problem is to have a central authority, called a_______.
a) key-search area (KSA). b) key-distribution center (KDC). c) key-terminal center (KTC). d) None of the above.
Write a variation equation for the statement. ![]() varies directly as the square root of
varies directly as the square root of ![]() and inversely as the cube of
and inversely as the cube of ![]() .
.
A. 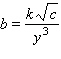
B. 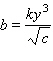
C. 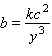
D. ![]()
E. ![]()
A package that includes hardware, software, and support from a single vendor is called a(n) ____ package.
A. model B. prototype C. turnkey D. integrated