Which of the following ethical frameworks is the study of the choices that have been made by individuals in the past?
A. Applied ethics
B. Descriptive ethics
C. Normative ethics
D. Deontological ethics
Answer: B
You might also like to view...
A ____ is really a physical folder or a redirection to a Uniform Resource Locator (URL) that points to a folder, so that it can be accessed over the Internet, an intranet, or VPN.
A. subordinate directory B. secondary directory C. virtual directory D. Web directory
Using a smart card and a one-time passcode is an example of which of the following authentication methods?
A. Single-factor authentication B. Multifactor authentication C. Multilayer authentication D. Cognitive password authentication
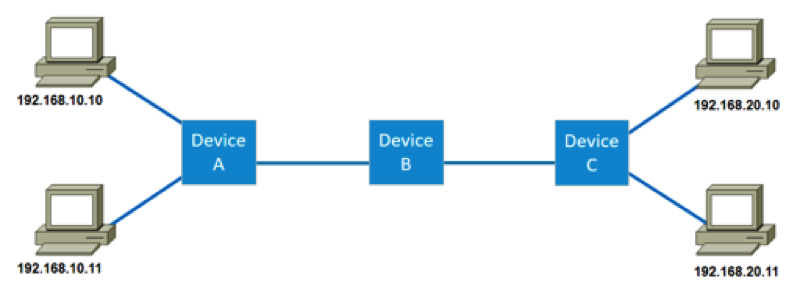
A. Layer 2 switch B. Router C. Bridge D. Repeater
When a computer transmits at the same time because it cannot sense that another computer on the WLAN is currently transmitting is referred to as the:
a. out of range problem b. collision problem c. hidden node problem d. controlled access problem e. media access problem