Wired equivalent privacy (WEP) is intended to guard one of the three CIA characteristics of information, namely ____.
A. confidentiality
B. integrity
C. availability
D. non-repudiation
Answer: A
Computer Science & Information Technology
You might also like to view...
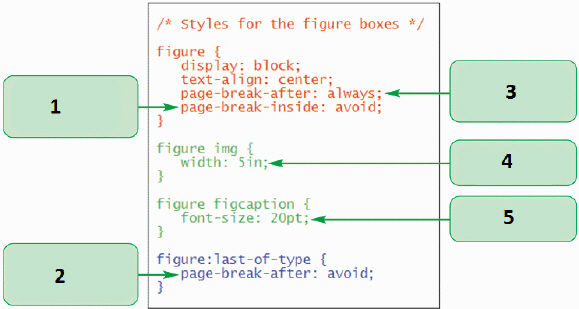 In the accompanying figure, which line of code does not add a page break after the last box?
In the accompanying figure, which line of code does not add a page break after the last box?
A. 2 B. 3 C. 1 D. 4
Computer Science & Information Technology
Pointing to a sizing handle of a chart allows you to move it. __________________________
Answer the following statement true (T) or false (F)
Computer Science & Information Technology
What should you use if you wish to execute two or more statements conditionally?
A. A switch statement. B. A block enclosed within a pair of curly braces. C. A defined sequence structure. D. A declared decision structure.
Computer Science & Information Technology
Multitasking
What will be an ideal response?
Computer Science & Information Technology