The role that is responsible for developing overall policies and procedures for database security is:
A) Data Administration.
B) Database Administration.
C) Database Development.
D) Accounting
A) Data Administration.
You might also like to view...
Which forms of inheritance are is-a relationships?
a. All forms of inheritance are is-a relationships. b. Only public and private. c. Only public and protected. d. Only public.
With multilevel page tables, a process’s PTE can be initialized when the process is first loaded, or each PTE can be initialized the first time its corresponding page is referenced. Similarly, the entire multilevel page table structure can be maintained in main memory, or parts of it can be sent to secondary storage. What are the costs and benefits of each approach?
What will be an ideal response?
On a computer with two or more CPUs, _____ is a technique in which each processor or core works on a different job.
A. ?parallel processing B. ?looped hosting C. ?multiprocessing D. ?file hosting
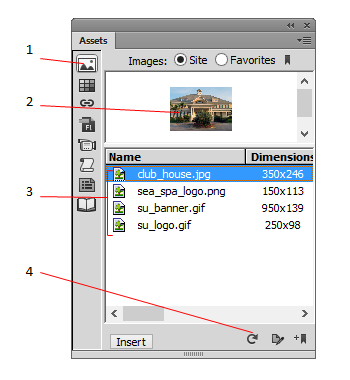
A. Images button B. Color button C. Upload button D. Websafe Color button