Comments can easily be modified
Indicate whether the statement is true or false
TRUE
You might also like to view...
Which of the following prevents XSS attacks?
A. access checks B. input validation C. fuzzing D. strong authentication
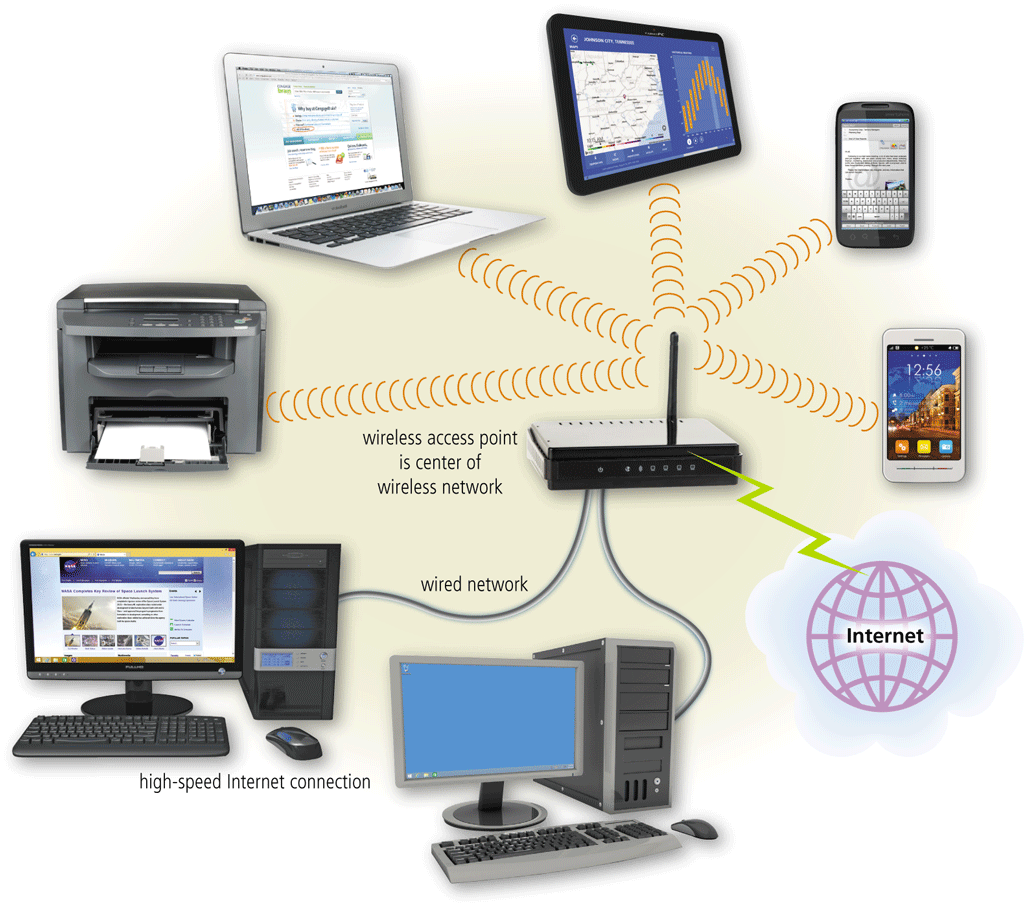
A. P2P B. SLAN C. WLAN D. FTP
A(n) _____ is not as flexible as a series of interviews, but it is less expensive, generally takes less time, and can involve a broad cross-section of people.
A. fishbone B. experiment C. survey D. research
Because only one template can be processed with any node, the processor must choose between competing templates for the same node. Using themodeattribute is one way of explicitly assigning a template to a specific node. Explain the default priority number rules used by an XSLT processor to determine template priority.
What will be an ideal response?