FIGURE AC 1-1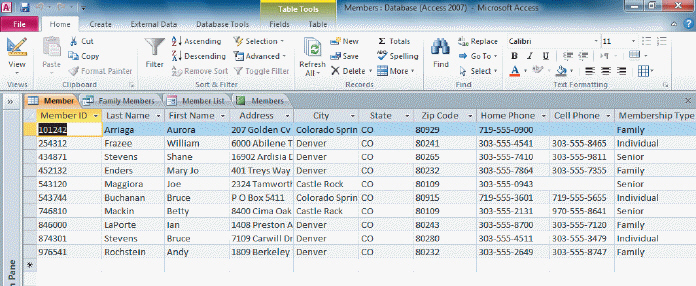
Referring to Figure AC 1-1 above, the word "Denver" is an example of a ____.
A. field
B. field value
C. field name
D. field selector
Answer: B
Computer Science & Information Technology
You might also like to view...
The most frequently used method to identify hidden vulnerabilities is a ____.
A. code execution B. design review C. code inspection D. sandbox review
Computer Science & Information Technology
When creating a calculated field using field names, Access automatically surrounds the field names with ________
A) braces { } B) parentheses ( ) C) brackets [ ] D) quotation marks " "
Computer Science & Information Technology
When planning a presentation, you should use ________ to ensure that your bullets are in the same grammatical form thereby helping your audience see the connection between your phrases
Fill in the blank(s) with correct word
Computer Science & Information Technology
The ________ Formula tool shows exactly how a formula executes
A) Review B) Analyze C) Interpret D) Evaluate
Computer Science & Information Technology