Masquerade, falsification, and repudiation are threat actions that cause __________ threat consequences.
A. unauthorized disclosure
B. deception
C. disruption
D. usurpation
B. deception
Computer Science & Information Technology
You might also like to view...
The active worksheet tab displays in bold
Indicate whether the statement is true or false
Computer Science & Information Technology
In Event Viewer which log contains events relating to running applications?
a. Security b. Setup c. System d. None of the above
Computer Science & Information Technology
FIGURE 1-2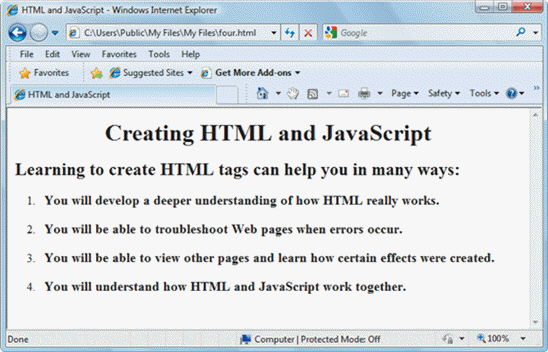 In Figure 1-2 above, the list shown is an example of a(n) ____.
In Figure 1-2 above, the list shown is an example of a(n) ____.
A. unordered list B. bulleted list C. ordered list D. either a. or b.
Computer Science & Information Technology
Briefly discuss displaying the formulas version of a worksheet.
What will be an ideal response?
Computer Science & Information Technology