__________ are third party audits of cloud services.
Fill in the blank(s) with the appropriate word(s).
Security assessments
You might also like to view...
A program that uses prompting messages to direct the user's input is running in ______.
a. batch mode b. arithmetic/logic mode c. interactive mode d. assembly language mode e. memory mode
A cookie is a(n) ________
A) example of a Java applet B) small text file placed on your computer C) small version of EDI D) example of an Active X control
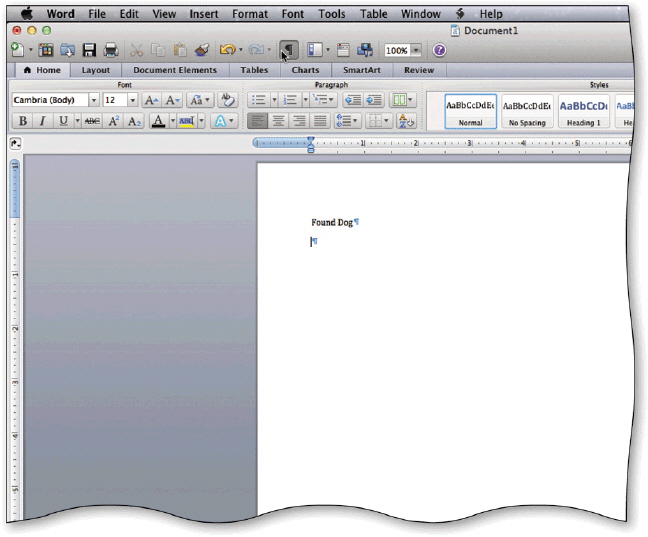 A(n) _________________________ is a character, like the ones in the accompanying figure, that Word displays on the screen but is not visible on a printed document.
A(n) _________________________ is a character, like the ones in the accompanying figure, that Word displays on the screen but is not visible on a printed document.
Fill in the blank(s) with the appropriate word(s).
Assuming a and b are objects with an overloaded == operator, rather than using the expression a == b we could have used the call ____.
A. a.operator == (b) B. a = b.operator C. operator = a.b D. b.operator = a