List five of the eight data entry methods mentioned in the book.
What will be an ideal response?
1. Keyboards
2. Bar codes
3. QR codes
4. Radio Frequency Identification (RFID)
5. Near Field Communication (NFC)
6. Optical character recognition (OCR)
7. Magnetic ink character recognition
8. Mark-sense forms
You might also like to view...
Which of the following is used when more than one choice may be selected?
A) check box B) sliders C) drop-down list box D) list box E) radio button
Analyze the following code:
``` public class A extends B { } class B { public B(String s) { } } ``` a. The program has a compile error because A does not have a default constructor. b. The program has a compile error because the default constructor of A invokes the default constructor of B, but B does not have a default constructor. c. The program would compile fine if you add the following constructor into A: A(String s) { } d. The program would compile fine if you add the following constructor
You can find the problems in this lab by examining the network configuration and looking for errors. The topology for this network is provided in Figure 1. Note: The switches in this network pass data but do not require configuration.
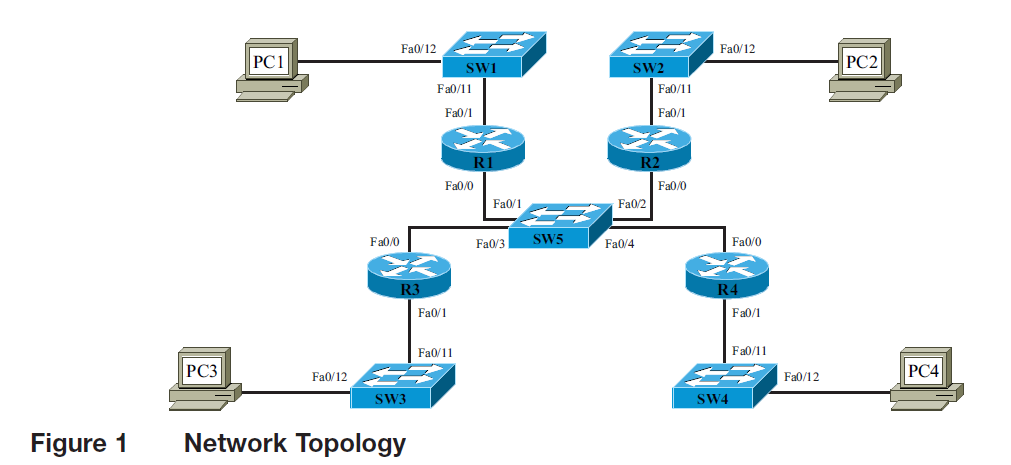
Table 1 is provided to record the problems discovered in the network configuration. As you find
each problem, add the discovered problem to Table 1, along with the actions to be taken to resolve
the problem.
Table 1 Record Root Causes and Solutions
1
2
3
4
5
6
7
Which of the following exchanges routing information between two autonomous systems?
A. EGP B. OSPF C. IGP D. EIGRP